Difference between revisions of "Template:Misfortune Cookie Upgrade Firmware"
Jump to navigation
Jump to search
m |
m (Xx176 moved page Template:Misfortune Cookie TP-Link Upgrades to Template:Misfortune Cookie Upgrade Firmware) |
||
| (2 intermediate revisions by the same user not shown) | |||
| Line 1: | Line 1: | ||
= ⚠ Vulnerable to Misfortune Cookie: | = ⚠ Vulnerable to Misfortune Cookie: Upgrade Firmware ⚠ = | ||
In December 2014 it was revealed that some | In December 2014 it was revealed that some versions of this TP-Link model are subject to hacking if they are running outdated firmware and if the remote access (ACL) is set to allow remote access. We documented this vulnerability on the [[Misfortune Cookie Vulnerability]] page. | ||
Read more on the Misfortune Cookie as reported in http://www.kb.cert.org/vuls/id/561444. | Read more on the Misfortune Cookie as reported in http://www.kb.cert.org/vuls/id/561444. | ||
Latest revision as of 11:20, 26 September 2019
⚠ Vulnerable to Misfortune Cookie: Upgrade Firmware ⚠
In December 2014 it was revealed that some versions of this TP-Link model are subject to hacking if they are running outdated firmware and if the remote access (ACL) is set to allow remote access. We documented this vulnerability on the Misfortune Cookie Vulnerability page.
Read more on the Misfortune Cookie as reported in http://www.kb.cert.org/vuls/id/561444.
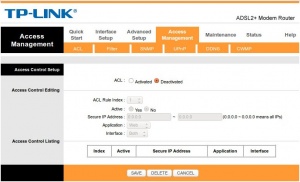
NCF Recommendation for this modem:
- Upgrade the Firmware to the lastest version if available.
- Also, Deactivate ACL from Access Management → ACL.
- If there is no firmware update for your version, replace the modem.