Spam
Spam is usually considered as unsolicited email in the form of marketing communications from corporations, organizations and individuals. A number of common types of spam are phishing and spoofing. They can be deceptive and may have malicious intent.
Phishing
A phishing attack is a message designed to trick a person into revealing sensitive information to the sender, or to deploy malicious software on the victim's computer. Some examples of phishing attacks are:
- You receive an e-mail stating you have won a prize and requires you to contact them to receive the prize.
- You receive an e-mail stating your account will be deactivated if you do not confirm your identity or usage.
- You receive an e-mail regarding a package being delivered to you which you did not request.
It is important to not respond to a phishing attack. Responding to a phishing attack can provide the senders with more personal information that can be used to target you further. Included in all e-mails is information like your e-mail address and the sending IP address, both of which an attacker can use to create increasingly more sophisticated phishing attempts.
Spoofing
Spoofing is the faking of email addresses to disguise who is sending the email to you. This is often used to make the sender appear to be a trusted source and make their e-mails more enticing. Because the core protocols for email do not prevent it, it is easy for someone to email you using a fake address for the sender. A common trick is to use the recipient's email address as the sender's as well, in other words the email will appear to come from you. This is used to fool spam filters as most people don't filter out their own address, but it is an easy-to-recognize indication that you are dealing with a spoofed address.
How to spot Spoofing and Phishing attempts
Emails on their own are safe to open, although their attachments may not be.
1. Make sure the sender is who they claim to be.
By hovering over the sender on Zimbra, you see a more information about the sender. In the picture above, the sender is claiming to be Zimbra. This e-mail is actually from @baruhotels.com, so Zimbra is a spoofed e-mail.
2. Make sure links go to a trusted domain
By hovering over the links on Zimbra, you can see the URL the link redirects to. In the picture above, the link claims to go to mail.ncf.ca, but actually links out to a dccitevital.org domain and is a phishing attempt
What to do with Phishing and Spoofing attempts?
Do not open any attachments!
Do not open any links!
Deleting the e-mail is the best option.
Reporting Phishing Emails
Phishing e-mails can be reported to the Office of the Privacy Commissioner of Canada through their website or by forwarding your e-mails to spam@fightspam.gc.ca.
Phishing links can be reported to Google at https://safebrowsing.google.com/safebrowsing/report_phish/?hl=en
Advanced E-mail tracking
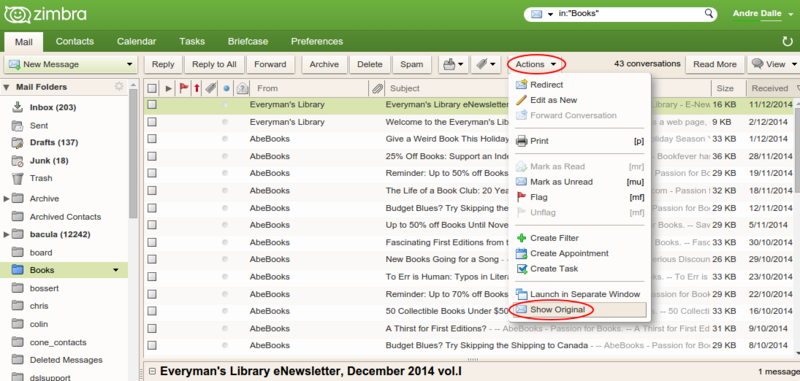
If you want to find out where the email is really coming from you need to check the email headers ("show original"), as shown here in Zimbra, NCF's webmail interface:
Here is an example of a set of email headers from a spoofed email:
Return-Path: youraddress@ncf.ca
Received: from localhost (LHLO mail.ncf.ca) (127.0.0.1) by melkor.ncf.ca
with LMTP; Wed, 16 Sep 2015 19:08:57 -0400 (EDT)
Received: from mail.ncf.ca (localhost [127.0.0.1])
by mail.ncf.ca (Postfix) with ESMTP id A8607A0547
for <fn352@ncf.ca>; Wed, 16 Sep 2015 19:08:55 -0400 (EDT)
X-Spam-Checker-Version: SpamAssassin 3https://help.ncf.ca/Spam#Zimbra_Filters.4.0 (2014-02-07) on melkor.ncf.ca
X-Spam-Level:
X-Spam-Status: No, score=-0.0 required=6.0 tests=BAYES_00,FSL_BULK_SIG,
HTML_IMAGE_ONLY_32,HTML_MESSAGE,PYZOR_CHECK,RCVD_IN_DNSWL_NONE,
RCVD_IN_MSPIKE_H2,T_REMOTE_IMAGE autolearn=no autolearn_force=no version=3.4.0
X-Spam-Virus: No
Received: from mx1.ncf.ca (pallando.ncf.ca [134.117.136.70])
by mail.ncf.ca (Postfix) with ESMTP id 942A5A051C
for <fn352@ncf.ca>; Wed, 16 Sep 2015 19:08:55 -0400 (EDT)
DKIM-Filter: OpenDKIM Filter v2.9.1 mail.ncf.ca 942A5A051C
Received: from mx1.ncf.ca (localhost [127.0.0.1])
by mx1.ncf.ca (Postfix) with ESMTP id 73766BEE75
for <fn352@ncf.ca>; Wed, 16 Sep 2015 19:08:55 -0400 (EDT)
X-Greylist: delayed 420 seconds by postgrey-1.34 at pallando; Wed, 16 Sep 2015 19:08:55 EDT
Received: from smtpg-pc.aruba.it (smtp217-pc.aruba.it [62.149.157.217])
by mx1.ncf.ca (Postfix) with ESMTP id 0D616BEE7C
for <fn352@ncf.ca>; Wed, 16 Sep 2015 19:08:54 -0400 (EDT)
Received: from WORLDST-UQ3K9Q0 ([181.26.209.230])
by smtpcm2-pc.aruba.it with bizsmtp
id Hz0g1r0094yo4K101z1GXd; Thu, 17 Sep 2015 01:01:54 +0200https://help.ncf.ca/Spam#Zimbra_Filters
The "received" sections show the IP addresses which the mail has travelled through and ultimately originates from. The IP addresses in the header are shown in bold to make them stand out. Because the bottom one is the originator, it can now be traced to see where it comes from.
Tracing IP addresses
Tracing IP addresses is fairly easy using tools like whois on Linux. They can also be traced through the websites of the IP registration authorities:
- ARIN (North America)
- RIPE NCC (Europe, the Middle East and Central Asia)
- APNIC (Asia Pacific)
- LACNIC (Latin American and Caribbean)
- AfriNIC (Africa)
- IP-adress.com (sic)
- Find-IP-address.org
If an address is not found in one registry, it will probably be in another one.
In the case of the header example above the IP address 181.26.209.230 traces to Telefonica de Argentina in Buenos Aires, Argentina, so you can be sure it did not originate with NCF and that the return address is spoofed.
Volunteer Dave - A Spoofing Story
An informative narrative written by one of our volunteers and his saga to expose spoofers when he found they were sending mail out from his address.
Someone is "Spoofing" your email address or has "hijacked" your email account. Please review the following for advice on what you can do to minimize the occurrences. Please try the suggestions and get back to us if you have further questions.
From: http://www.pcworld.com/article/2927993/what-to-do-when-your-email-address-sends-spam.html
What’s worse than getting spam? Unwittingly sending it. When bogus and probably malware-laden advertising goes out in your name, you look bad. And you get flooded with bounced messages from dead addresses that some crook attempted to spam in your name.
The good news: You’re not sending out spam. Neither is your computer or your IP address. But the bad news can still be pretty bad.
If spam is going out from your email address, the address has been either spoofed or hijacked. Either way, the spam isn’t going out from your computer, and probably not from the criminal’s computer, either. It’s probably going out from an unknowing victim’s malware-infected PC.
Spoofing an email address is, in a sense, forging it. The criminal sends out mail with your From address, even though they have no access to your account.
There’s really no solution to spoofing. Fortunately, for their own reasons, cybercrooks tend to change spoofed addresses frequently. The annoyance will disappear soon.
Hijacking is worse. In this case, the criminal takes control of your account. They can read your mail, and they can target people you know when they spam. And they can lock you out of your own account.
Fortunately, you can do something about hijacking.
As soon as you discover that your address is spamming people, try to change your password…immediately. If you succeed, you’ve fixed the problem.
But if your mail service rejects your password, the problem is serious. The hijacker has changed the password first and now controls your account.
If you’re still connected and can receive mail, try to login on another computer or using your browser’s private mode. When the login fails, try the service’s “Forgot your password” or “Need help” link. The service will email you a new password. Hopefully, you’ll get it before the bad guy.
If that fails, you’ll have to contact the mail service and discuss the problem. Here are the links for Gmail and Microsoft’s Outlook . If you’re using another service, you’ll have to find the right address yourself.
Have you been using the same password for other services? If so, change them as soon as possible.
Once you’ve got everything under control, email apologies to everyone who received, or might have received, spam apparently coming from you.
Finally, follow these steps to make sure this doesn’t happen again:
Use strong, long passwords that people can’t guess.
Use different passwords for different services, and keep track of them with a password manager.
Set up 2-step verification for your service. You should find instructions on the service’s setup or options screen.
Never email your password to anyone, and I mean anyone.
Shortly after I wrote this article, my daughter's Gmail account was hacked, and everyone she knew received messages telling them to "Click on the document below and log in with your email and password to view it." I gave her the Gmail URL above, and within a few minutes she had her account back.
Here is a link to another good article about this "From:spoofing"
Dave
Zimbra Filters
Zimbra offers powerful filtering options for blocking spammers. Zimbra is build into our email back end, so even if you're not using the Zimbra web client to access your emails, Zimbra filters will still work. This means that even if you're using a popular mail client like outlook, gmail, or your phone, Zimbra filters still offer protection against spammers. The simplest way to block a spammer is by setting up a filter for the email address that the spammer is using to send you spam.
Follow these instructions to set up a filter to block emails from a specific address. In this example the hypothetical spammer is sending us emails from the address: daily@spam.com.
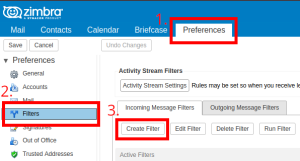
- Log into your Zimbra webclient, then go to Preferences > Filters.
- Click on "New Filter" to create a new filter. You can make as many filters as you'd like.
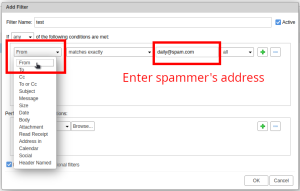
- Under "If any of the following conditions are met" set the first option to "from", and leave all other drop down options as default.
- In the text field to the right, enter the spammer's entire email address, in this example we're using daily@spam.com, but this will be specific to who is sending you spam.
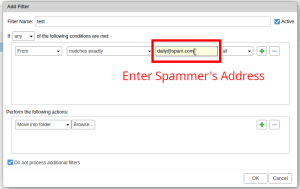
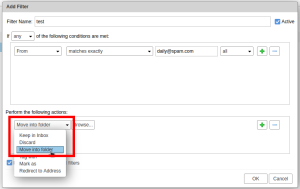
- Under "Perform the following actions" select "Move into folder".
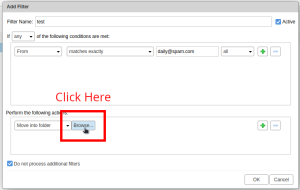
- Click on "Browse..." to select the folder you'd like to send the emails to.
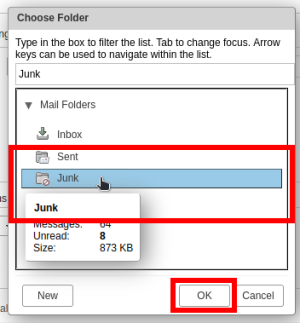
- Click on the "Junk" folder, then click on "Ok" to save
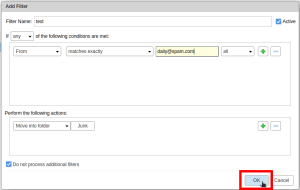
- At this point your filter should be set up as the following:
- filter condition = "From" "Matches exactly" "Spammer's email address" "all".
- filter action = "Move into folder" "Junk".
- Click on the "Ok" button to save the filter.
- You should now see your new filter under "Active Filters". Your filter is now working on your incoming mail!
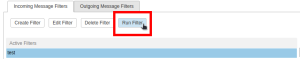
- You can run your filter by clicking on your filter's name, then clicking "Run Filter".
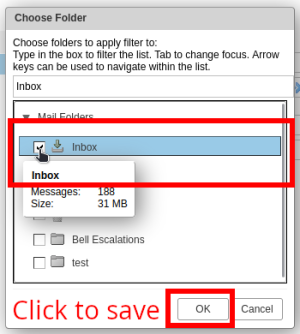
- Choose which folder you'd like to run the filter on. Then click "OK" to run the filter.
External links
- Phishing quiz on Open DNS
- Email spoofing on Wikipedia
- NCF's 2018 workshop File:SWaC - Spam+Phishing.pdf